
초기 설정
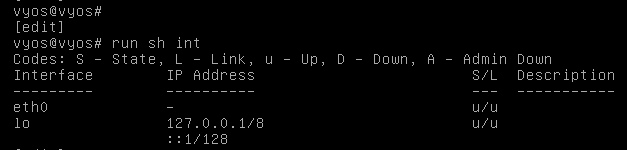
- eth0
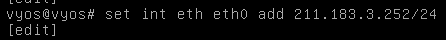
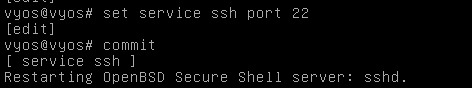
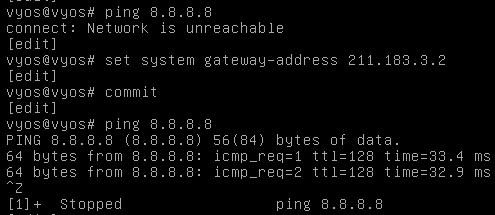
- xshell 연결
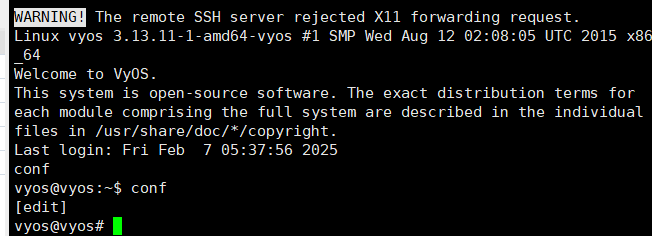
- virtual network connect 끊기

- eth1
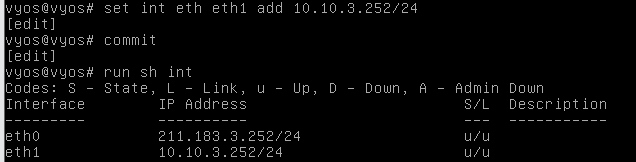
- eth2
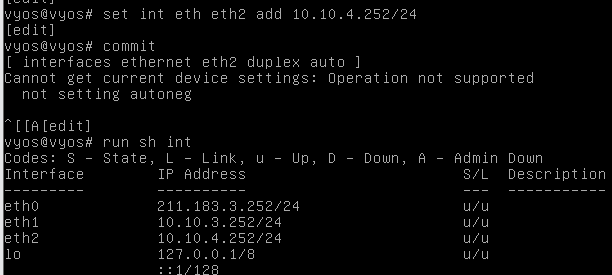
- web ip랑 vm대역 재설정
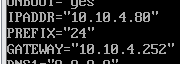
- mint ip랑 vm대역 재설정
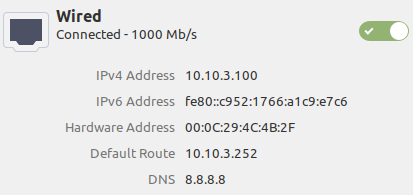
- client ip
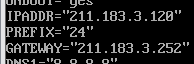
vyos@vyos# set int eth eth0 description public
[edit]
vyos@vyos# set int eth eth1 description private
[edit]
vyos@vyos# set int eth eth2 description dmz
[edit]
vyos@vyos# commit
private에서 public(1, 2번)
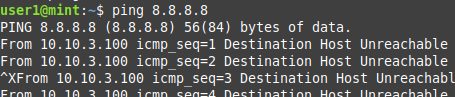
mint
vyos@vyos# set nat source rule 10 source address 10.10.3.0/24
[edit]
vyos@vyos# set nat source rule 10 outbound-interface eth0
[edit]
vyos@vyos# set nat source rule 10 translation address 211.183.3.252
[edit]
vyos@vyos# commit
DNAT 설정
vyos@vyos# set nat destination rule 200 inbound-interface eth0
[edit]
vyos@vyos# set nat destination rule 200 translation address 10.10.3.100
[edit]
vyos@vyos# set nat destination rule 200 translation port 22
[edit]
vyos@vyos# set nat destination rule 200 protocol tcp
[edit]
vyos@vyos# set nat destination rule 200 destination port 2222
[edit]
vyos@vyos# commit
private 안으로 들어가는 거 설정(1번)
vyos@vyos# set firewall name PUBLIC_TO_PRIVATE rule 10 action accept
[edit]vyos@vyos# set firewall name PUBLIC_TO_PRIVATE rule 10 state established enable[edit]vyos@vyos# set firewall name PUBLIC_TO_PRIVATE rule 10 state related enable[edit]vyos@vyos# set firewall name PUBLIC_TO_PRIVATE rule 10 protocol all
[edit]
vyos@vyos# set firewall name PUBLIC_TO_PRIVATE rule 10 protocol tcp
[edit]
vyos@vyos# set firewall name PUBLIC_TO_PRIVATE rule 10 destination port ssh
[edit] #정책 설정
vyos@vyos# set zone-policy zone private from public firewall name PUBLIC_TO_PRIVATE
[edit] # 정책 적용
private 나가는 public으로 나가는 설정(2번)
vyos@vyos# set firewall name PRIVATE_TO_PUBLIC rule 20 action accept
[edit]
vyos@vyos# set firewall name PRIVATE_TO_PUBLIC rule 20 state established enable
[edit]
vyos@vyos# set firewall name PRIVATE_TO_PUBLIC rule 20 state related enable
[edit]
vyos@vyos# set firewall name PRIVATE_TO_PUBLIC rule 20 protocol all
[edit]
vyos@vyos# set zone-policy zone public from private firewall name PRIVATE_TO_PUBLIC
[edit]
vyos@vyos# commit
[edit]
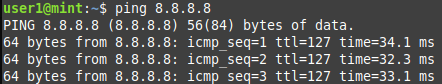
DMZ
web
vyos@vyos# set nat source rule 20 source address 10.10.4.0/24
[edit]
vyos@vyos# set nat source rule 20 outbound-interface eth0
[edit]
vyos@vyos# set nat source rule 20 translation address 211.183.3.252
[edit]
vyos@vyos# commit

DNAT 설정
ftp
vyos@vyos# set nat destination rule 100 inbound-interface eth0
[edit]
vyos@vyos# set nat destination rule 100 translation address 10.10.4.80
[edit]
vyos@vyos# set nat destination rule 100 protocol tcp
[edit]vyos@vyos# set nat destination rule 100 destination port ftp [edit]
vyos@vyos# set nat destination rule 300 destination port 20,21
[edit]
tftp
vyos@vyos# set nat destination rule 300 inbound-interface eth0
[edit]
vyos@vyos# set nat destination rule 300 translation address 10.10.4.80
[edit]
vyos@vyos# set nat destination rule 300 protocol udp
[edit] vyos@vyos# set nat destination rule 300 destination port 69 [edit]
vyos@vyos# set nat destination rule 300 translation port 69
[edit]
http
vyos@vyos# set nat destination rule 400 inbound-interface eth0
[edit]
vyos@vyos# set nat destination rule 400 translation address 10.10.4.80
[edit]
vyos@vyos# set nat destination rule 400 translation port 80
[edit]
vyos@vyos# set nat destination rule 400 protocol tcp
[edit]
vyos@vyos# set nat destination rule 400 destination port 80
[edit]
ssh
vyos@vyos# set nat destination rule 500 inbound-interface eth0
[edit]
vyos@vyos# set nat destination rule 500 translation address 10.10.4.80
[edit]
vyos@vyos# set nat destination rule 500 translation port 22
[edit]
vyos@vyos# set nat destination rule 500 protocol tcp
[edit]
vyos@vyos# set nat destination rule 500 destination port 222
[edit]
vyos@vyos# commit
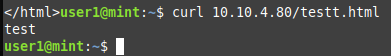
ZONE 기반 방화벽 설정
vyos@vyos# set zone-policy zone public interface eth0
[edit]
vyos@vyos# set zone-policy zone private interface eth1
[edit]
vyos@vyos# set zone-policy zone dmz interface eth2
[edit]
vyos@vyos# commit
private에서 DMZ로 향하는 정책(3, 4번 정책)
private에서 dmz로 향하는 정책(3번)
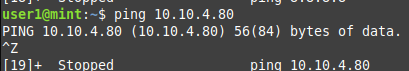
vyos@vyos# set firewall name PRIVATE_TO_DMZ rule 30 action accept
[edit]
vyos@vyos# set firewall name PRIVATE_TO_DMZ rule 30 protocol tcp
[edit]
vyos@vyos# set zone-policy zone dmz from private firewall name PRIVATE_TO_DMZ
[edit] vyos@vyos# set firewall name PRIVATE_TO_DMZ rule 30 destination port http [edit]
vyos@vyos# set firewall name PRIVATE_TO_DMZ rule 30 destination port 80,23
[edit]
private 에서 dmz로 향하는 정책(4번)
****왜 4번 정책을 넣어줘야 ping이 가는 것 일까? 3번 해주면 가야 되는 것 아닐까?
들어가는 곳이랑 나가는 곳이 달라서 그런가?
vyos@vyos# set firewall name DMZ_TO_PRIVATE rule 40 action accept
[edit]
vyos@vyos# set firewall name DMZ_TO_PRIVATE rule 40 state established enable
[edit]
vyos@vyos# set firewall name DMZ_TO_PRIVATE rule 40 state related enable
[edit]
vyos@vyos# set firewall name DMZ_TO_PRIVATE rule 40 protocol all
[edit]
vyos@vyos# set zone-policy zone private from dmz firewall name DMZ_TO_PRIVATE
[edit]
vyos@vyos# commit
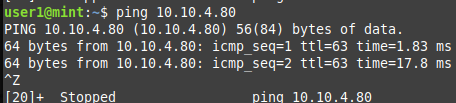
DMZ공간에서 public 설정(5, 6번)
- public client server
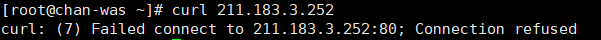
DMZ공간에서 public 공간으로 나가는 것 방어(5번)
vyos@vyos# set firewall name DMZ_TO_PUBLIC rule 50 action accept
[edit] vyos@vyos# set firewall name DMZ_TO_PUBLIC rule 50 state established enable [edit]vyos@vyos# set firewall name DMZ_TO_PUBLIC rule 50 protocol all [edit]
vyos@vyos# set firewall name DMZ_TO_PUBLIC rule 50 state related enable [edit]
vyos@vyos# set zone-policy zone public from dmz firewall name DMZ_TO_PUBLIC
[edit]
vyos@vyos# commit
[edit]
public에서 dmz로 가는 ftp 트래픽을 위한 설정(6번, ftp)
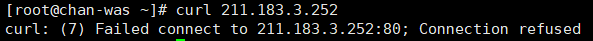
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 60 action accept
[edit]
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 60 protocol tcp
[edit]
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 60 destination port 20, 21
[edit]
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 60 state established enable [edit]
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 60 state related enable [edit]
vyos@vyos# set zone-policy zone dmz from public firewall name PUBLIC_TO_DMZ
[edit]
vyos@vyos# commit
전부 차단하지만 연관 있는 트래픽은 밖으로 내보내줘야됨
- 61번 rule은 오로지 5번 정책을 위한 rule임
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 61 action accept
[edit]
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 61 state established enable
[edit]
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 61 state related enable
[edit]
vyos@vyos# set firewall name PUBLIC_TO_DMZ rule 61 protocol all
[edit]
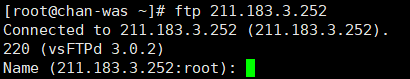
전체 설정
'AWS Cloud School 8기 > 서버가상화_클라우드 이미지' 카테고리의 다른 글
| Site-to-Site VPN (2) | 2025.02.17 |
|---|---|
| Server-Client VPN/ 와이파이 대역 활용한 실습 (0) | 2025.02.13 |
| VyOS Firewall (0) | 2025.02.11 |
| ACL(ACcess-List) (0) | 2025.02.09 |
| VyOS/ (VyOS nat 해제) (0) | 2025.02.06 |





